before they
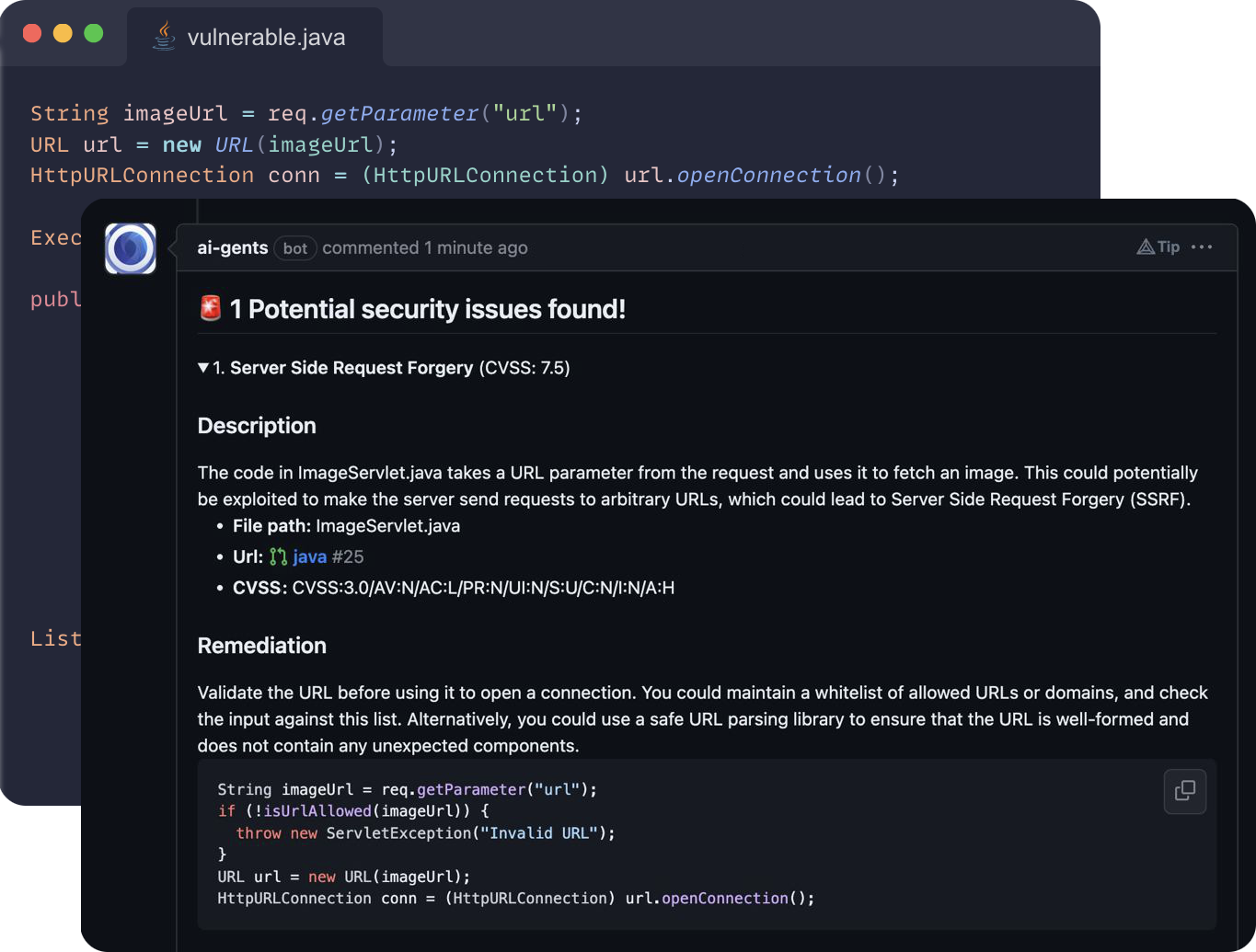
What is Naxus?
Automated Vulnerability Lifecycle
We go beyond simple detection. Naxus automates the entire vulnerability lifecycle, from identification to resolution, with deep insight into exposed assets and proof-of-concept exploits. Our system minimizes false positives by validating real exploitability, while also guiding you with precise remediation suggestions. Stay secure effortlessly as every step of the process is handled with intelligence and precision.


Attack Path Discovery
See your code’s vulnerabilities the way an attacker would. Naxus maps attack paths across complex code flows and interdependent components, tracing weaknesses through the intricate web of your software. This full-spectrum visibility empowers your team to make proactive, data-driven security decisions before issues become breaches.
Context-Aware Detection
Not all vulnerabilities are equal. Naxus performs deep contextual analysis of your codebase (understanding relationships, behavior, and intent) to detect sophisticated issues that span multiple files or layers. By reducing false positives and surfacing what truly matters, we make vulnerability detection smarter, faster, and far more effective.

More than a monitoring solution
Real-time.
Instantly detects and reports security weaknesses as code is committed, providing immediate feedback to developers.
Historical data.
Maintains a historical record of vulnerabilities, aiding in trend analysis and demonstrating security improvements over time.
User-friendly.
Features an intuitive, user-friendly interface designed to make vulnerability management accessible to all team members.
GitHub Integration.
Seamlessly integrates with GitHub to make it easy for teams to incorporate security checks into their existing development workflows.
Agent-ready.
Autonomous AI agents independently verify detected vulnerabilities, validating exploitability and prioritizing real risks with precision, so your team stays focused without the noise of false positives.
Contextual Analysis Levels.
Multiple levels of contextual analysis, allowing teams to customize the depth of code scrutiny according to their specific requirements.